- Software
- Blockchain
- Web3 product
- Smart Contracts
- Mobile app
- Web platform
- AWS Cloud
- NFT marketplace
- DeFi
- Fintech
- AI product
- dApp
- Crypto wallet
Rumble Fish helps entrepreneurs build and launch bespoke digital products.
We take care of the technology, so you can focus on your business
Join the ecosystem
of our satisfied customers:









of our satisfied customers:










Who we are?
Hi there! We're Rumble Fish - a team of world-class experts in bespoke software development. Our engineers are highly skilled in blockchain, cloud solutions, and defi/fintech development. Our strength and pride is the ability to take ownership of the entire development process and be a true partner and advisor for our customers. Our mission is to craft state-of-the-art digital products using battle-tested technologies. Try us!
40uniquely skilled devs
1pet-friendly office
8years in business
42projects
999passion for coding
What do we do?
Software Development Services and Skills for your needs
Our team is well-versed and experienced in various blockchain development tools and technologies. Our unique skillset allows us to be at the forefront of Web3 development services so if you’re looking for a trusted IT partner to boost your decentralized product - look no further!
We deliver production-ready zero-knowledge proof solutions that actually ship to mainnet, specializing in custom ZK development, rollup scaling solutions, and privacy-preserving smart contracts that reduce processing times from hours to minutes. Try us!
We build fast, compliant, and cost-effective blockchain solutions on the XRP Ledger. From payment systems and tokenization platforms to enterprise DeFi applications, our team delivers production-ready systems that work when billions are on the line.
We build smart contracts that handle real business complexity without the usual blockchain headaches. From DeFi protocols to custom on-chain systems, we deliver production-ready solutions that scale.
Decentralized Finance (DeFi) development requires an extensive amount of blockchain knowledge, as well as a great understanding of financial mechanisms. We’ve got both that bases covered! Our team has successfully built an impressive number of DeFi products like cryptocurrency exchanges, dApps, lending protocols, or staking platforms. Try us!
Our experienced team will take your AWS cloud solutions to the next level. AWS provides purpose-built tools to support your needs, and it is the preferred choice for any blockchain project. From the plethora of cloud tools and solutions offered by Amazon Web Services, we’ll help you choose and implement the ones that serve your business the best way possible.
AI chatbots can bring value to a wide range of industries by enhancing customer interactions, streamlining processes, and improving overall efficiency. We'll craft a perfect AI assistant for your product.
Need realistic data for AI training, testing, or product development—but privacy, scale, or availability is blocking you? We engineer custom synthetic data solutions that capture the complexity of real-world data without the constraints. From multi-modal generation to domain-specific datasets, we build what platforms can't deliver.
We build custom AI knowledge management systems that turn your scattered enterprise knowledge into instant, accurate answers - no more employees wasting their valuable time hunting through SharePoint and Slack for information. Unlike platforms that trap you in subscriptions, we engineer RAG solutions specifically for your data and security requirements, then hand you complete ownership of the source code and infrastructure.
Looking for a skilled team to help you build an advanced fintech platform able to compete with the biggest in the game? At Rumble Fish, we’ve got what it takes to engineer innovative financial technology systems. We offer end-to-end fintech software development, consulting, and expertise.
Our experts provide you with knowledge, skills, and experience that elevates every project to another level. We’ll gladly take ownership of the entire process and guide you and your team through the intricacies of cutting-edge technology development.
If you’re in need of professional web development services, look no further! Rumble Fish's talented team has extensive experience in delivering top-tier web apps and websites with the use of battle-tested tools and technologies like React or Nest. We know just the right solutions to exceed your business requirements.
Whether you need an Android, an IOS app, or both, the Rumble Fish team is here to help you deliver the beautiful and efficient mobile product that your customers will simply love to use! We craft fast and secure mobile apps with a wow factor to help our customers grow their businesses and reach their goals quicker.
If you're looking for a team capable of turning your product concept into a beautiful and technologically intricate digital solution - look no further! Rumble Fish is your trusted software development partner ready to take you through the entire process of custom digital product creation - from the early stages of ideation to the post-launch support. Whether you're on a mission to build a mobile app, a Web3 product, or an advanced platform - we are here for you!
We design sleek, intuitive, and highly effective interfaces to help you overcome your business challenges. After carefully evaluating and understanding your requirements we switch to the designing mode - the end goal is the beautiful digital solution that people love to use!
Testimonials
See what our customers say about working with us“
Latest case studyBridging Tari to Ethereum: WXTM & Secure Tokenization
Bridging Tari to Ethereum: WXTM & Secure Tokenization
Tari is an innovative L1 protocol focused on digital assets and privacy-preserving smart contracts. As a relatively new blockchain entering the crypto landscape, Tari faced a critical challenge: how to integrate their native XTM tokens with the broader DeFi ecosystem to enable trading, liquidity provision, and participation in decentralized finance protocols.
Collaboration timeframe:2 months
Services:Smart Contract Development, Blockchain Development, DevOps, Front-End Development, Back-End Development, AWS Cloud Solutions
We're trusted by global innovators and leaders.Join them!
TURNTABLE
A hybrid of a social network and a music appTURNTABLE
MAKERDAO
The first truly decentralized stablecoin crypto on EthereumMAKERDAO
ZBAY
A private inbox, wallet, and marketplace all in oneZBAY
VERIFYID
An identity verification MVPVERIFYID
Rumblefish Blog Running Claude as a Backend Service: How We Build AI-Powered Web Applications on AWS
Running Claude as a Backend Service: How We Build AI-Powered Web Applications on AWS By Marek KowalskiThe AI revolution is transforming how we build software. But there's a gap between the impressive capabilities of large language models and the practical expectations of business users who need familiar, reliable interfaces. At Rumble Fish, we've developed an architecture that bridges this gap - running Claude as a backend microservice that powers traditional-looking web applications with AI-driven intelligence.
## The Traditional Way: Claude as a Developer Tool
Most developers know Claude as either a built-in code assistant in popular IDEs like VS Code or Cursor, or as a standalone desktop application where you type prompts and get responses. These interfaces work great for technical users who are comfortable with conversational AI. But what about everyone else?
## The Challenge: AI for Non-Technical Users
At Rumble Fish, we've seen growing interest from clients who want to automate work that requires thinking and creativity - tasks that go beyond simple rule-based automation. Content analysis, document processing, research synthesis, and decision support - these are areas where AI excels.
**The challenge?** Most business users expect traditional browser-based interfaces. They're not comfortable typing prompts into a chat window and interpreting unstructured responses. They want buttons, forms, dashboards, and predictable workflows. How do we reconcile the creative, flexible nature of AI agents with the structured expectations of enterprise software?
## Our Solution: Claude as a Microservice
We run Claude as a containerized service on AWS. Here's how it works:
### The Container Setup
We package Claude using the Claude SDK inside a Docker container, deployed as an ECS task. Each container includes:
\- A checkout of a repository containing a \`CLAUDE.md\` file
\- Skill definitions and scripts specific to the client's use case
\- All the context the agent needs to perform its specialized tasks
The \`CLAUDE.md\` file acts as the agent's instruction manual - defining its role, output formats, and behavioral guidelines. This gives us precise control over how the agent operates while maintaining the flexibility that makes AI valuable.
### Persistence Through S3 Sync
At the start and end of each task, we run \`aws s3 sync\` to synchronize the agent's working directory with an S3 bucket. This simple mechanism provides:
\- **State persistence**: The agent accumulates knowledge between invocations
\- **Audit trail**: Every file the agent creates is preserved
\- **Easy integration**: Other services can read the agent's outputs directly from S3
## The Architecture in Detail
When a user interacts with our web interface, here's the sequence of events:
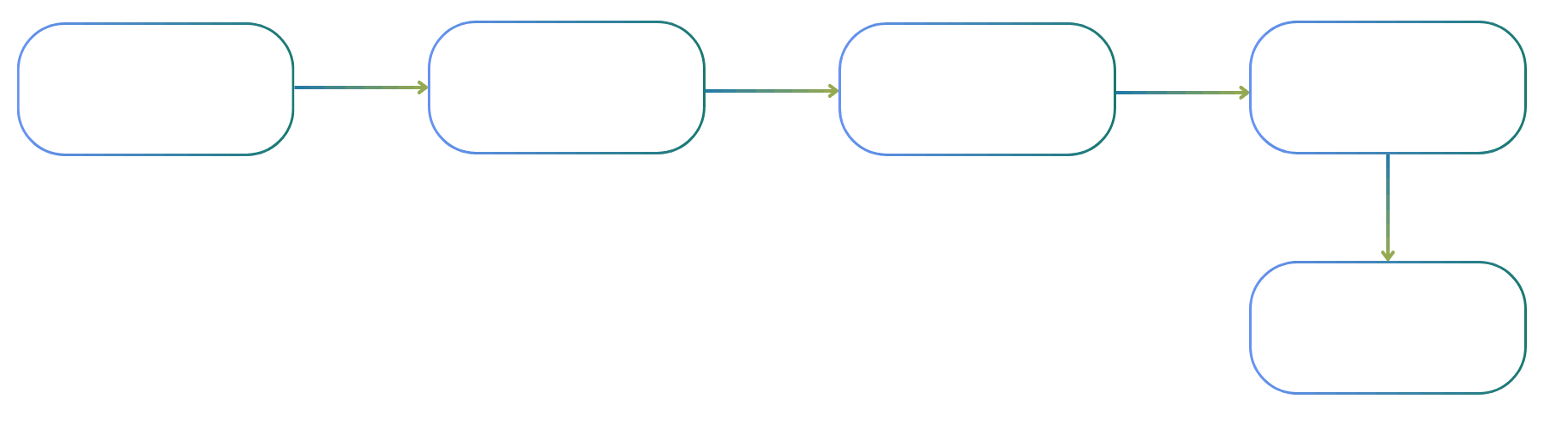
1. **User Action:** The user clicks a button or submits a form in our React Admin interface
2. **Backend Processing:** A Lambda function (exposed via API Gateway) receives the request and constructs a prompt for the agent
3. **Queue Management:** The prompt goes into an SQS FIFO queue, ensuring ordered processing and preventing concurrent executions
4. **Agent Execution:** An ECS task spins up, the agent processes the prompt, and generates its outputs
5. **Result Storage:** Output files are synced back to S3, task metadata (ARNs, status) is stored in our database, and logs end up in another S3 bucket
### Why SQS FIFO?
The FIFO queue is crucial. While the agent is running, queue consumption is blocked. This prevents race conditions and ensures the agent always works with a consistent state. It also gives us natural backpressure - if requests come in faster than the agent can process them, they queue up gracefully.
### Structured Output, Flexible Presentation
We instruct the agent (via \`CLAUDE.md\`) to save its analysis in markdown format at predictable locations. This gives us:
\- **No custom UI development:** Markdown renders beautifully with minimal effort
\- **Flexibility:** The agent can structure its output however makes sense for the task
\- **Readability**: Non-technical users can read and understand the results directly
The admin interface simply presents the contents of the S3 bucket. It doesn't need to understand what the agent does; it just displays what the agent produces.
## The Result: AI That Feels Like Software
The end product looks and feels like a standard web application. Users see familiar interfaces - lists, forms, buttons, dashboards. They don't need to learn prompt engineering or understand how AI works. But behind that familiar facade, Claude is doing work that would be impossible with traditional software: synthesizing information, making judgment calls, generating creative solutions, and adapting to edge cases that no developer anticipated.
It's the best of both worlds: the reliability and usability of traditional software, combined with the intelligence and adaptability of modern AI.
## Proven in Production
At Rumble Fish, we're currently running three different projects using this architecture. Each solves a different problem, but they share the same pattern:
* Automate work that requires thinking, not just data shuffling
* Present results through interfaces that traditional users understand
* Maintain full auditability and control over the AI's behavior
This approach is becoming our go-to solution for a wide range of problems. The common thread: bridging intelligent automation with familiar user experiences.
## Is This Right for Your Organization?
If your team is exploring AI adoption but worried about user acceptance, complex integrations, or unpredictable behavior, **this architecture might be the answer.** It lets you harness AI capabilities while maintaining the control and predictability that enterprise environments demand.
**Thinking about bringing AI into your workflows?** [Book a free consultation](https://rumblefish.dev/contact) with our team. We'll help you identify opportunities and design an approach that fits your needs.
By Marek KowalskiThe AI revolution is transforming how we build software. But there's a gap between the impressive capabilities of large language models and the practical expectations of business users who need familiar, reliable interfaces. At Rumble Fish, we've developed an architecture that bridges this gap - running Claude as a backend microservice that powers traditional-looking web applications with AI-driven intelligence.
## The Traditional Way: Claude as a Developer Tool
Most developers know Claude as either a built-in code assistant in popular IDEs like VS Code or Cursor, or as a standalone desktop application where you type prompts and get responses. These interfaces work great for technical users who are comfortable with conversational AI. But what about everyone else?
## The Challenge: AI for Non-Technical Users
At Rumble Fish, we've seen growing interest from clients who want to automate work that requires thinking and creativity - tasks that go beyond simple rule-based automation. Content analysis, document processing, research synthesis, and decision support - these are areas where AI excels.
**The challenge?** Most business users expect traditional browser-based interfaces. They're not comfortable typing prompts into a chat window and interpreting unstructured responses. They want buttons, forms, dashboards, and predictable workflows. How do we reconcile the creative, flexible nature of AI agents with the structured expectations of enterprise software?
## Our Solution: Claude as a Microservice
We run Claude as a containerized service on AWS. Here's how it works:
### The Container Setup
We package Claude using the Claude SDK inside a Docker container, deployed as an ECS task. Each container includes:
\- A checkout of a repository containing a \`CLAUDE.md\` file
\- Skill definitions and scripts specific to the client's use case
\- All the context the agent needs to perform its specialized tasks
The \`CLAUDE.md\` file acts as the agent's instruction manual - defining its role, output formats, and behavioral guidelines. This gives us precise control over how the agent operates while maintaining the flexibility that makes AI valuable.
### Persistence Through S3 Sync
At the start and end of each task, we run \`aws s3 sync\` to synchronize the agent's working directory with an S3 bucket. This simple mechanism provides:
\- **State persistence**: The agent accumulates knowledge between invocations
\- **Audit trail**: Every file the agent creates is preserved
\- **Easy integration**: Other services can read the agent's outputs directly from S3
## The Architecture in Detail
When a user interacts with our web interface, here's the sequence of events:

1. **User Action:** The user clicks a button or submits a form in our React Admin interface
2. **Backend Processing:** A Lambda function (exposed via API Gateway) receives the request and constructs a prompt for the agent
3. **Queue Management:** The prompt goes into an SQS FIFO queue, ensuring ordered processing and preventing concurrent executions
4. **Agent Execution:** An ECS task spins up, the agent processes the prompt, and generates its outputs
5. **Result Storage:** Output files are synced back to S3, task metadata (ARNs, status) is stored in our database, and logs end up in another S3 bucket
### Why SQS FIFO?
The FIFO queue is crucial. While the agent is running, queue consumption is blocked. This prevents race conditions and ensures the agent always works with a consistent state. It also gives us natural backpressure - if requests come in faster than the agent can process them, they queue up gracefully.
### Structured Output, Flexible Presentation
We instruct the agent (via \`CLAUDE.md\`) to save its analysis in markdown format at predictable locations. This gives us:
\- **No custom UI development:** Markdown renders beautifully with minimal effort
\- **Flexibility:** The agent can structure its output however makes sense for the task
\- **Readability**: Non-technical users can read and understand the results directly
The admin interface simply presents the contents of the S3 bucket. It doesn't need to understand what the agent does; it just displays what the agent produces.
## The Result: AI That Feels Like Software
The end product looks and feels like a standard web application. Users see familiar interfaces - lists, forms, buttons, dashboards. They don't need to learn prompt engineering or understand how AI works. But behind that familiar facade, Claude is doing work that would be impossible with traditional software: synthesizing information, making judgment calls, generating creative solutions, and adapting to edge cases that no developer anticipated.
It's the best of both worlds: the reliability and usability of traditional software, combined with the intelligence and adaptability of modern AI.
## Proven in Production
At Rumble Fish, we're currently running three different projects using this architecture. Each solves a different problem, but they share the same pattern:
* Automate work that requires thinking, not just data shuffling
* Present results through interfaces that traditional users understand
* Maintain full auditability and control over the AI's behavior
This approach is becoming our go-to solution for a wide range of problems. The common thread: bridging intelligent automation with familiar user experiences.
## Is This Right for Your Organization?
If your team is exploring AI adoption but worried about user acceptance, complex integrations, or unpredictable behavior, **this architecture might be the answer.** It lets you harness AI capabilities while maintaining the control and predictability that enterprise environments demand.
**Thinking about bringing AI into your workflows?** [Book a free consultation](https://rumblefish.dev/contact) with our team. We'll help you identify opportunities and design an approach that fits your needs. Beyond Code: How Claude is Transforming Knowledge Work
Beyond Code: How Claude is Transforming Knowledge Work By Marek KowalskiAt Rumble Fish, a software development agency, we live in an industry defined by constant change. Adapt or become irrelevant - that's the reality we face every day. When AI coding assistants emerged, we were early adopters. But what surprised us wasn't Claude's ability to write code. It was everything else.
## The Work That Couldn't Be Automated
Every agency has tasks that seem immune to automation: analyzing datasets to find patterns, correlating information from multiple sources, or making sense of unstructured data. This work requires judgment, context, and the ability to handle exceptions. It's why we always assumed it needed humans.
**We were wrong.**
## A Different Kind of Intelligence
Claude doesn't just follow scripts. Its reasoning capabilities allow it to adapt when things don't go as expected. Feed it messy data, and it figures out what you meant. Throw it an edge case, and it works through it logically. You could almost call it creative - not in the artistic sense, but in the problem-solving sense.
We've built repositories that define skills Claude can use. These aren't rigid automation pipelines. They're flexible frameworks where Claude applies judgment within boundaries we set. **The results have been remarkable.**
## The New Division of Labor
The efficiency gain isn't about replacing humans. It's about changing what humans do.
**Before:** A team member spends hours on repetitive analysis, losing focus, getting tired, and making mistakes on the mundane cases while staying sharp for the interesting ones.
**Now:** Claude handles the repetitive work with unwavering consistency. It never gets bored. It maintains the same level of attention on case number 500 as it did on case number 1. And when it hits those edge cases requiring genuine creativity? It still delivers.
Humans review results, refine prompts, and handle the truly novel situations. It's a better use of everyone's capabilities.
## Claude in Practice
### Lead Generation
This use case was put together in just a few days by some of our engineers as part of their AI training. Historically, our marketing and sales team spent considerable time scouring the web for potential clients. It's such a time and labor-intensive task that it almost felt like a waste of effort.
**We built a Claude repository with skills that scrape publicly available job boards and identify relevant opportunities.** This goes far beyond what a traditional search query could do. We're looking for companies that offer remote work, are open to hiring an agency, and need expertise in technologies we specialize in: blockchain, ZKP, AWS, and AI. Claude turned out to be remarkably good at understanding job posts and rating them according to the rules we defined.
The result? We can now process a flood of information that was previously too massive to handle manually. This has opened an entirely new sales channel for our agency.
### Cloud Deployment for Team Collaboration
Most people encounter Claude as an IDE extension or a standalone desktop application. But there's another way: running the Claude SDK inside a Docker container.
This allows us to deploy Claude as an ECS task on AWS, which unlocks something powerful for team collaboration. **Multiple team members can share the same knowledge base and continuously update the skills and rules defined in the repository.** When someone refines a prompt or adds a new capability, everyone benefits immediately.
The result is a tool that effectively learns from the humans using it. Each improvement compounds, and the system gets smarter over time - not through model updates, but through collective human insight captured in the repository.
[Find out more about AI-powered enterprise knowledge management solutions.](https://www.rumblefish.dev/services/ai-knowledge-management-solutions/)
## Looking Forward
We believe this represents a fundamental shift in how knowledge work gets done. Not automation in the traditional sense, not rigid rules and brittle scripts. Something more flexible. Something that can think. **The agencies and teams that figure this out will operate at a different level of efficiency. The ones that don't will find themselves wondering how their competitors move so fast.**
We're still learning what's possible. But one thing is clear: Claude isn't just a coding tool. It's a thinking tool. And that changes everything.
By Marek KowalskiAt Rumble Fish, a software development agency, we live in an industry defined by constant change. Adapt or become irrelevant - that's the reality we face every day. When AI coding assistants emerged, we were early adopters. But what surprised us wasn't Claude's ability to write code. It was everything else.
## The Work That Couldn't Be Automated
Every agency has tasks that seem immune to automation: analyzing datasets to find patterns, correlating information from multiple sources, or making sense of unstructured data. This work requires judgment, context, and the ability to handle exceptions. It's why we always assumed it needed humans.
**We were wrong.**
## A Different Kind of Intelligence
Claude doesn't just follow scripts. Its reasoning capabilities allow it to adapt when things don't go as expected. Feed it messy data, and it figures out what you meant. Throw it an edge case, and it works through it logically. You could almost call it creative - not in the artistic sense, but in the problem-solving sense.
We've built repositories that define skills Claude can use. These aren't rigid automation pipelines. They're flexible frameworks where Claude applies judgment within boundaries we set. **The results have been remarkable.**
## The New Division of Labor
The efficiency gain isn't about replacing humans. It's about changing what humans do.
**Before:** A team member spends hours on repetitive analysis, losing focus, getting tired, and making mistakes on the mundane cases while staying sharp for the interesting ones.
**Now:** Claude handles the repetitive work with unwavering consistency. It never gets bored. It maintains the same level of attention on case number 500 as it did on case number 1. And when it hits those edge cases requiring genuine creativity? It still delivers.
Humans review results, refine prompts, and handle the truly novel situations. It's a better use of everyone's capabilities.
## Claude in Practice
### Lead Generation
This use case was put together in just a few days by some of our engineers as part of their AI training. Historically, our marketing and sales team spent considerable time scouring the web for potential clients. It's such a time and labor-intensive task that it almost felt like a waste of effort.
**We built a Claude repository with skills that scrape publicly available job boards and identify relevant opportunities.** This goes far beyond what a traditional search query could do. We're looking for companies that offer remote work, are open to hiring an agency, and need expertise in technologies we specialize in: blockchain, ZKP, AWS, and AI. Claude turned out to be remarkably good at understanding job posts and rating them according to the rules we defined.
The result? We can now process a flood of information that was previously too massive to handle manually. This has opened an entirely new sales channel for our agency.
### Cloud Deployment for Team Collaboration
Most people encounter Claude as an IDE extension or a standalone desktop application. But there's another way: running the Claude SDK inside a Docker container.
This allows us to deploy Claude as an ECS task on AWS, which unlocks something powerful for team collaboration. **Multiple team members can share the same knowledge base and continuously update the skills and rules defined in the repository.** When someone refines a prompt or adds a new capability, everyone benefits immediately.
The result is a tool that effectively learns from the humans using it. Each improvement compounds, and the system gets smarter over time - not through model updates, but through collective human insight captured in the repository.
[Find out more about AI-powered enterprise knowledge management solutions.](https://www.rumblefish.dev/services/ai-knowledge-management-solutions/)
## Looking Forward
We believe this represents a fundamental shift in how knowledge work gets done. Not automation in the traditional sense, not rigid rules and brittle scripts. Something more flexible. Something that can think. **The agencies and teams that figure this out will operate at a different level of efficiency. The ones that don't will find themselves wondering how their competitors move so fast.**
We're still learning what's possible. But one thing is clear: Claude isn't just a coding tool. It's a thinking tool. And that changes everything.
Check a piece of expert knowledge
 Running Claude as a Backend Service: How We Build AI-Powered Web Applications on AWS
Running Claude as a Backend Service: How We Build AI-Powered Web Applications on AWS By Marek Kowalski
By Marek KowalskiAI
 Beyond Code: How Claude is Transforming Knowledge Work
Beyond Code: How Claude is Transforming Knowledge Work By Marek Kowalski
By Marek KowalskiAI
Have an idea?
Let’s work
together!We will answer any questions you may have related to your startup journey!Do you prefer e-mail?
hello@rumblefish.pl
together!We will answer any questions you may have related to your startup journey!Do you prefer e-mail?
hello@rumblefish.pl


RUMBLEFISH POLAND SP Z O.O.Filipa Eisenberga 11/3 31-523 Kraków, Polska
NIP: 6772425725REGON: 368368380KRS: 0000696628
P: +48 601 265 364E: hello@rumblefish.dev
Copyright © 2026 RumblefishServicesBlockchain Software DevelopmentZero-Knowledge Proof DevelopmentXRPL Blockchain DevelopmentSmart Contract DevelopmentDeFi DevelopmentAWS Cloud SolutionsAI Chat Assistant DevelopmentSynthetic Data GenerationFintech Software DevelopmentDedicated Development TeamsWeb developmentMobile developmentIT Services for startupUI/UXRust Web App DevelopmentView all services
CareersJoin Our Team



